
Recently I had Tim Nash, the WordPress platform lead at 34SP.com, speak at the local WordPress meetup I help run. It’s the third time Tim has spoken at the meetup, and in the past he has spoken about site security and performance but this time he spoke about a handful of case studies of hackings; how the sites were exploited and what could be done to mitigate the vulnerability.
Tim’s talk was essentially a scaryhelpful introduction to penetration testing (or pentesting) with a WordPress flavor. It got me thinking just how secure the sites I manage are and perhaps I should really look deeper into site security further than just the fundamentals of WordPress security.
What is Penetration Testing
The deeper you get into site security, the darker it gets. Penetration testing is the practice of simulating an attack on a system, network, app or website to identify vulnerabilities that might be exploited.
In simple terms, you become the hacker to protect your site. But that means any testing you perform needs to be authorized by the site or system owner (read: your boss or client needs to give the thumbs up), and to avoid arrest and criminal charges (keep in mind I’m not a lawyer), I wouldn’t recommend putting into practice any of these techniques or using these tools for nefarious purposes.
If you are penetration testing a website, please perform it on an exact copy of production on your local development environment, where possible. You won’t put the production site under unnecessary load and you won’t be mistaken as a hacker! 👮
Penetration testing typically is either performed with full knowledge of the system (‘white box’), to allow finding as many vulnerabilities as possible, or by simulating a real attack without any knowledge of the system (‘black box’).
Why do it
So why go to all the trouble of further testing? You might not care much if your personal blog is exploited – just take it down and clean it up at your leisure. However, ecommerce and business-critical sites require security to be a primary concern.
Regular penetration testing has some important benefits:
- Preemptively find vulnerabilities, especially as plugins and themes are updated and new ones are installed
- Prevent costly downtime for fixing and restoring sites after hacks by addressing these vulnerabilities before they’re exploited
- Avoid regulatory penalties and reputational damage by keeping customer data secure
Recommended Penetration Testing Tools
The best piece of advice for WordPress site security is to keep everything updated – including WordPress core, themes, and plugins. As Tim pointed out –
It’s better to fix issues due to theme or plugin updates than to have a hacked site to fix
The alternative is to keep running outdated code that could contain vulnerabilities that have seen been patched.
Which brings us to the first tool in our testing arsenal.
WPScan
WPScan is a free, black box WordPress vulnerability scanner that interrogates your site to see what plugins you have installed, checks the version and reports if those plugins have a known vulnerability using data sourced from the WPScan Vulnerability Database.
WPScan is a great tool to use if you’ve just inherited a site and want to check if the plugins or themes have any known issues. DigitalOcean has a good tutorial for using WPScan.
Themes can be especially susceptible to vulnerabilities due to the bad, once-popular practice of bundling plugins with themes. Bad because if you use a theme like that, unless the theme developer updates the plugins regularly in their theme and releases theme version updates, it’s unlikely that patched versions of vulnerable plugins will make it to your site. (Revolution Slider anyone?)
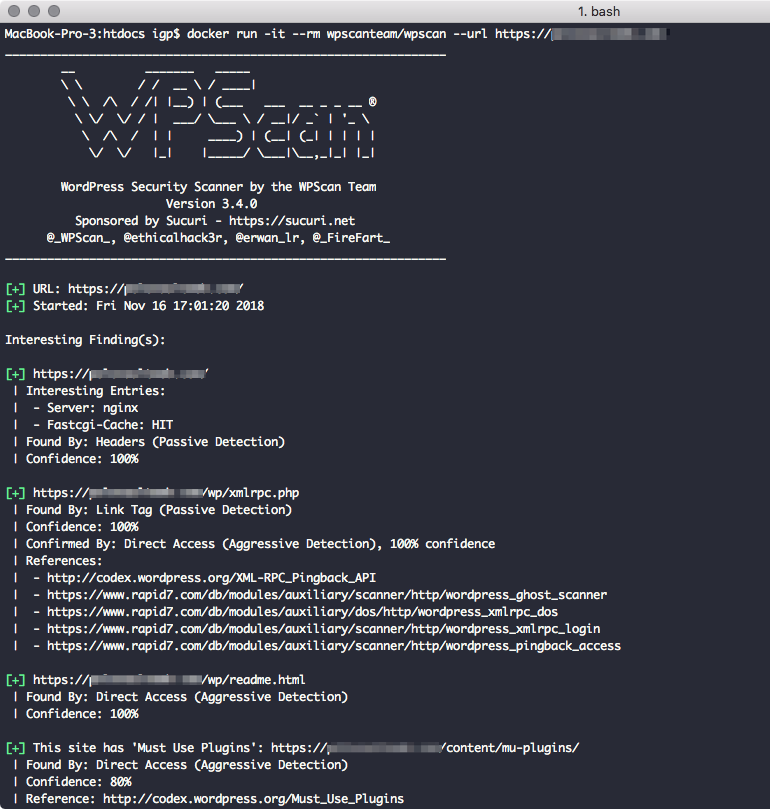
As mentioned before, nothing compares to just keeping everything up-to-date. If you don’t enable automatic theme and plugin updates for your WordPress site then it’s worth running WPScan automatically on sites and even signing up to the free email alerts from the WPScan Vulnerability Database.
sqlmap
sqlmap automates the process of detecting SQL injection vulnerabilities in sites. If you know that a site accepts data through the GET, POST or Cookie parameters or through the HTTP User-Agent request header, then there is the potential that it can be affected by a SQL injection vulnerability.
It’s a command line tool which you point at your site with a vast array of arguments and modifiers that let you test for vulnerabilities. For example, to get sqlmap to see if we can gain access to the database, you use the dbs argument pointing at a URL which accepts a query string:
sqlmap -u http://mysite.dev/products/?cat=15 --dbs
Why should you be concerned about SQL injection? Let’s say you have a plugin that accepts data through a query string and doesn’t properly sanitize that data before being used to query the database, then a malicious user could pass SQL conditions to the query string value, or even stacked SQL statements (think http://mysite.com/?id=1;DROP database 😬).
If you are developing a plugin or code that accepts user data via forms or query strings then carefully consider how you sanitize and check the data before using it in your backend. Use sqlmap to try and hack your own WordPress code to test its robustness.
PHPStan
Tim also mentioned PHPStan, which is a PHP static analysis tool which you can point at your codebase to help find errors and bugs in your code. I’d seen Gilbert mention he’d recently run it on the Laravel codebase of SpinupWP with some good results, so I was eager to point it at some WordPress sites:
Since @github has been down all day I spent some time setting up @phpstan in our latest Laravel project. Sure enough, it found a couple of bugs. https://t.co/3ZsANRhIjN
— Gilbert Pellegrom (@gilbitron) October 22, 2018
Unfortunately the tool is more geared towards object-oriented codebases which WordPress isn’t.
There are alternatives for code analysis for WordPress projects. There are WordPress rules for PHP_CodeSniffer which checks your code is following defined standards to help elimate possible code problems. Also services like Scrutinizer will continually analyze your code to find issues, bugs and enforce coding styles. There’s also the Tide project to help improve WordPress plugin and theme code quality.
Actively monitoring the quality of your code during development will reduce the likelihood of vulnerable code reaching production.
Kali
If you’re serious about penetration testing then take a look at Kali. Kali is a complete testing platform installed as a virtual machine where you can run a whole suite of tools and perform all the steps to detect, exploit and fix vulnerabilities (for nice purposes of course!).
WordFence has a great guide of the steps to take as part of a penetration test using the Kali platform:
- Reconnaissance
- Scanning
- Exploitation
- Mitigation
There are a bunch of other tools around to help with testing such as OWASP ZAP, Metasploit and BurpSuite. But whatever your tool of choice, ultimately the goal of penetration testing is the mitigation part. If you can find and recreate security holes then you can fix them.
Wrapping Up
I hope that’s given you a good introduction to the advanced practice of penetration testing and why it’s worth investing in for the security of your WordPress site.
Do you perform penetration testing on your WordPress sites or for clients? Have I missed any tools you find useful? Let us know in the comments below.